#include <Governance.h>
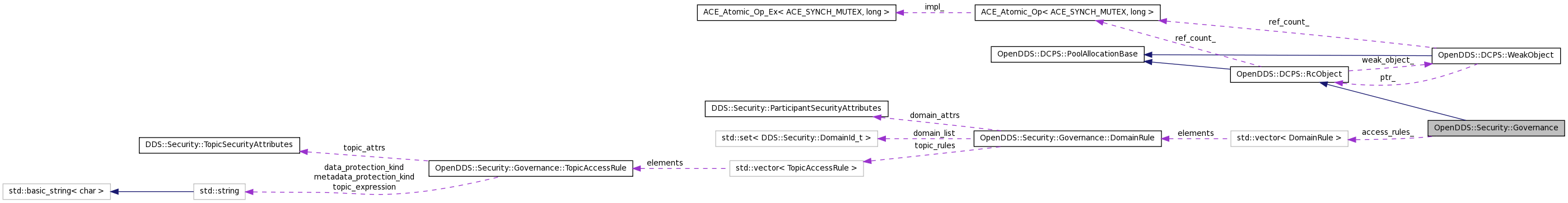
Classes | |
| struct | DomainRule |
| struct | TopicAccessRule |
Public Types | |
| typedef DCPS::RcHandle < Governance > | shared_ptr |
| typedef std::vector < TopicAccessRule > | TopicAccessRules |
| typedef std::vector< DomainRule > | GovernanceAccessRules |
Public Member Functions | |
| Governance () | |
| int | load (const SSL::SignedDocument &doc) |
| GovernanceAccessRules & | access_rules () |
Private Attributes | |
| GovernanceAccessRules | access_rules_ |
Definition at line 19 of file Governance.h.
| typedef std::vector<DomainRule> OpenDDS::Security::Governance::GovernanceAccessRules |
Definition at line 39 of file Governance.h.
Definition at line 22 of file Governance.h.
| typedef std::vector<TopicAccessRule> OpenDDS::Security::Governance::TopicAccessRules |
Definition at line 31 of file Governance.h.
| OpenDDS::Security::Governance::Governance | ( | ) |
Definition at line 21 of file Governance.cpp.
00021 : access_rules_() 00022 { 00023 00024 }
| GovernanceAccessRules& OpenDDS::Security::Governance::access_rules | ( | ) | [inline] |
Definition at line 45 of file Governance.h.
References access_rules_.
00046 { 00047 return access_rules_; 00048 }
| int OpenDDS::Security::Governance::load | ( | const SSL::SignedDocument & | doc | ) |
Definition at line 26 of file Governance.cpp.
References access_rules_, ACE_TEXT(), DDS::Security::ParticipantSecurityAttributes::allow_unauthenticated_participants, atoi(), OpenDDS::Security::Governance::TopicAccessRule::data_protection_kind, OpenDDS::Security::Governance::DomainRule::domain_attrs, OpenDDS::Security::Governance::DomainRule::domain_list, OpenDDS::DCPS::unique_ptr< T, Deleter >::get(), OpenDDS::Security::SSL::SignedDocument::get_original_minus_smime(), DDS::Security::ParticipantSecurityAttributes::is_access_protected, DDS::Security::TopicSecurityAttributes::is_discovery_protected, DDS::Security::ParticipantSecurityAttributes::is_discovery_protected, DDS::Security::TopicSecurityAttributes::is_liveliness_protected, DDS::Security::ParticipantSecurityAttributes::is_liveliness_protected, DDS::Security::TopicSecurityAttributes::is_read_protected, DDS::Security::ParticipantSecurityAttributes::is_rtps_protected, DDS::Security::TopicSecurityAttributes::is_write_protected, LM_ERROR, OpenDDS::Security::Governance::TopicAccessRule::metadata_protection_kind, parser, DDS::Security::ParticipantSecurityAttributes::plugin_participant_attributes, DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_BUILTIN_IS_DISCOVERY_ENCRYPTED, DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_DISCOVERY_ORIGIN_AUTHENTICATED, DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_LIVELINESS_ENCRYPTED, DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_LIVELINESS_ORIGIN_AUTHENTICATED, DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_RTPS_ENCRYPTED, DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_RTPS_ORIGIN_AUTHENTICATED, DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_VALID, ACE_OS::strcasecmp(), strcmp(), OpenDDS::Security::Governance::TopicAccessRule::topic_attrs, OpenDDS::Security::Governance::TopicAccessRule::topic_expression, and OpenDDS::Security::Governance::DomainRule::topic_rules.
00027 { 00028 using XML::XStr; 00029 static const char* gMemBufId = "gov buffer id"; 00030 00031 DCPS::unique_ptr<xercesc::XercesDOMParser> parser(new xercesc::XercesDOMParser()); 00032 00033 if (!parser) { 00034 ACE_DEBUG((LM_ERROR, ACE_TEXT( 00035 "(%P|%t) AccessControlBuiltInImpl::load_governance_file: Governance XML DOMParser Exception.\n"))); 00036 return -1; 00037 } 00038 00039 parser->setValidationScheme(xercesc::XercesDOMParser::Val_Always); 00040 parser->setDoNamespaces(true); // optional 00041 parser->setCreateCommentNodes(false); 00042 00043 DCPS::unique_ptr<xercesc::ErrorHandler> errHandler((xercesc::ErrorHandler*) new xercesc::HandlerBase()); 00044 parser->setErrorHandler(errHandler.get()); 00045 00046 // buffer for parsing 00047 00048 std::string cleaned; 00049 doc.get_original_minus_smime(cleaned); 00050 00051 xercesc::MemBufInputSource contentbuf((const XMLByte*) cleaned.c_str(), 00052 cleaned.size(), 00053 gMemBufId); 00054 00055 try { 00056 parser->parse(contentbuf); 00057 } 00058 catch (const xercesc::XMLException& toCatch) { 00059 char* message = xercesc::XMLString::transcode(toCatch.getMessage()); 00060 ACE_DEBUG((LM_ERROR, ACE_TEXT( 00061 "(%P|%t) AccessControlBuiltInImpl::load_governance_file: Exception message is %C.\n"), message)); 00062 xercesc::XMLString::release(&message); 00063 return -1; 00064 } 00065 catch (const xercesc::DOMException& toCatch) { 00066 char* message = xercesc::XMLString::transcode(toCatch.msg); 00067 ACE_DEBUG((LM_ERROR, ACE_TEXT( 00068 "(%P|%t) AccessControlBuiltInImpl::load_governance_file: Exception message is %C.\n"), message)); 00069 xercesc::XMLString::release(&message); 00070 return -1; 00071 } 00072 catch (...) { 00073 ACE_DEBUG((LM_ERROR, ACE_TEXT( 00074 "(%P|%t) AccessControlBuiltInImpl::load_governance_file: Unexpected Governance XML Parser Exception.\n"))); 00075 return -1; 00076 } 00077 00078 // Successfully parsed the governance file 00079 00080 xercesc::DOMDocument* xmlDoc = parser->getDocument(); 00081 00082 xercesc::DOMElement* elementRoot = xmlDoc->getDocumentElement(); 00083 if ( !elementRoot ) throw(std::runtime_error( "empty XML document" )); 00084 00085 // Find the domain rules 00086 xercesc::DOMNodeList * domainRules = xmlDoc->getElementsByTagName(XStr("domain_rule")); 00087 00088 for (XMLSize_t r = 0; r < domainRules->getLength(); r++) { 00089 Governance::DomainRule rule_holder_; 00090 rule_holder_.domain_attrs.plugin_participant_attributes = 0; 00091 00092 // Pull out domain ids used in the rule. We are NOT supporting ranges at this time 00093 xercesc::DOMNodeList * ruleNodes = domainRules->item(r)->getChildNodes(); 00094 00095 for (XMLSize_t rn = 0; rn < ruleNodes->getLength(); rn++) { 00096 const XStr dn_tag = ruleNodes->item(rn)->getNodeName(); 00097 00098 if ("domains" == dn_tag) { 00099 xercesc::DOMNodeList * domainIdNodes = ruleNodes->item(rn)->getChildNodes(); 00100 00101 for (XMLSize_t did = 0; did < domainIdNodes->getLength(); did++) { 00102 if ("id" == XStr(domainIdNodes->item(did)->getNodeName())) { 00103 const XMLCh* t = domainIdNodes->item(did)->getTextContent(); 00104 unsigned int i; 00105 if (xercesc::XMLString::textToBin(t, i)) { 00106 rule_holder_.domain_list.insert(i); 00107 } 00108 } 00109 else if ("id_range" == XStr(domainIdNodes->item(did)->getNodeName())) { 00110 int min_value = 0; 00111 int max_value = 0; 00112 xercesc::DOMNodeList * domRangeIdNodes = domainIdNodes->item(did)->getChildNodes(); 00113 00114 for (XMLSize_t drid = 0; drid < domRangeIdNodes->getLength(); drid++) { 00115 if (strcmp("min", xercesc::XMLString::transcode(domRangeIdNodes->item(drid)->getNodeName())) == 0) { 00116 min_value = atoi(xercesc::XMLString::transcode(domRangeIdNodes->item(drid)->getTextContent())); 00117 } 00118 else if (strcmp("max", xercesc::XMLString::transcode(domRangeIdNodes->item(drid)->getNodeName())) == 0) { 00119 max_value = atoi(xercesc::XMLString::transcode(domRangeIdNodes->item(drid)->getTextContent())); 00120 00121 if ((min_value == 0) || (min_value > max_value)) { 00122 ACE_DEBUG((LM_ERROR, ACE_TEXT( 00123 "(%P|%t) AccessControlBuiltInImpl::load_governance_file: Governance XML Domain Range invalid.\n"))); 00124 return -1; 00125 } 00126 00127 for (int i = min_value; i <= max_value; i++) { 00128 rule_holder_.domain_list.insert(i); 00129 } 00130 } 00131 } 00132 } 00133 } 00134 00135 } 00136 } 00137 00138 // Process allow_unauthenticated_participants 00139 xercesc::DOMNodeList * allow_unauthenticated_participants_ = 00140 xmlDoc->getElementsByTagName(XStr("allow_unauthenticated_participants")); 00141 char * attr_aup = xercesc::XMLString::transcode(allow_unauthenticated_participants_->item(0)->getTextContent()); 00142 rule_holder_.domain_attrs.allow_unauthenticated_participants = (ACE_OS::strcasecmp(attr_aup,"false") == 0 ? false : true); 00143 xercesc::XMLString::release(&attr_aup); 00144 00145 // Process enable_join_access_control 00146 xercesc::DOMNodeList * enable_join_access_control_ = 00147 xmlDoc->getElementsByTagName(XStr("enable_join_access_control")); 00148 char * attr_ejac = xercesc::XMLString::transcode(enable_join_access_control_->item(0)->getTextContent()); 00149 rule_holder_.domain_attrs.is_access_protected = ACE_OS::strcasecmp(attr_ejac, "false") == 0 ? false : true; 00150 xercesc::XMLString::release(&attr_ejac); 00151 00152 // Process discovery_protection_kind 00153 xercesc::DOMNodeList * discovery_protection_kind_ = 00154 xmlDoc->getElementsByTagName(XStr("discovery_protection_kind")); 00155 char * attr_dpk = xercesc::XMLString::transcode(discovery_protection_kind_->item(0)->getTextContent()); 00156 if (ACE_OS::strcasecmp(attr_dpk, "NONE") == 0) { 00157 rule_holder_.domain_attrs.is_discovery_protected = false; 00158 } else if (ACE_OS::strcasecmp(attr_dpk, "SIGN") == 0) { 00159 rule_holder_.domain_attrs.is_discovery_protected = true; 00160 } else if (ACE_OS::strcasecmp(attr_dpk, "ENCRYPT") == 0) { 00161 rule_holder_.domain_attrs.is_discovery_protected = true; 00162 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_BUILTIN_IS_DISCOVERY_ENCRYPTED; 00163 } else if (ACE_OS::strcasecmp(attr_dpk, "SIGN_WITH_ORIGIN_AUTHENTICATION") == 0) { 00164 rule_holder_.domain_attrs.is_discovery_protected = true; 00165 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_DISCOVERY_ORIGIN_AUTHENTICATED; 00166 } else if (ACE_OS::strcasecmp(attr_dpk, "ENCRYPT_WITH_ORIGIN_AUTHENTICATION") == 0) { 00167 rule_holder_.domain_attrs.is_discovery_protected = true; 00168 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_BUILTIN_IS_DISCOVERY_ENCRYPTED; 00169 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_DISCOVERY_ORIGIN_AUTHENTICATED; 00170 } 00171 xercesc::XMLString::release(&attr_dpk); 00172 00173 // Process liveliness_protection_kind 00174 xercesc::DOMNodeList * liveliness_protection_kind_ = 00175 xmlDoc->getElementsByTagName(XStr("liveliness_protection_kind")); 00176 char * attr_lpk = xercesc::XMLString::transcode(liveliness_protection_kind_->item(0)->getTextContent()); 00177 if (ACE_OS::strcasecmp(attr_lpk, "NONE") == 0) { 00178 rule_holder_.domain_attrs.is_liveliness_protected = false; 00179 } else if (ACE_OS::strcasecmp(attr_lpk, "SIGN") == 0) { 00180 rule_holder_.domain_attrs.is_liveliness_protected = true; 00181 } else if (ACE_OS::strcasecmp(attr_lpk, "ENCRYPT") == 0) { 00182 rule_holder_.domain_attrs.is_liveliness_protected = true; 00183 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_LIVELINESS_ENCRYPTED; 00184 } else if (ACE_OS::strcasecmp(attr_lpk, "SIGN_WITH_ORIGIN_AUTHENTICATION") == 0) { 00185 rule_holder_.domain_attrs.is_liveliness_protected = true; 00186 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_LIVELINESS_ORIGIN_AUTHENTICATED; 00187 } else if (ACE_OS::strcasecmp(attr_lpk, "ENCRYPT_WITH_ORIGIN_AUTHENTICATION") == 0) { 00188 rule_holder_.domain_attrs.is_liveliness_protected = true; 00189 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_LIVELINESS_ENCRYPTED; 00190 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_LIVELINESS_ORIGIN_AUTHENTICATED; 00191 } 00192 xercesc::XMLString::release(&attr_lpk); 00193 00194 // Process rtps_protection_kind 00195 xercesc::DOMNodeList * rtps_protection_kind_ = 00196 xmlDoc->getElementsByTagName(XStr("rtps_protection_kind")); 00197 char * attr_rpk = xercesc::XMLString::transcode(rtps_protection_kind_->item(0)->getTextContent()); 00198 00199 if (ACE_OS::strcasecmp(attr_rpk, "NONE") == 0) { 00200 rule_holder_.domain_attrs.is_rtps_protected = false; 00201 } else if (ACE_OS::strcasecmp(attr_rpk, "SIGN") == 0) { 00202 rule_holder_.domain_attrs.is_rtps_protected = true; 00203 } else if (ACE_OS::strcasecmp(attr_rpk, "ENCRYPT") == 0) { 00204 rule_holder_.domain_attrs.is_rtps_protected = true; 00205 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_RTPS_ENCRYPTED; 00206 } else if (ACE_OS::strcasecmp(attr_rpk, "SIGN_WITH_ORIGIN_AUTHENTICATION") == 0) { 00207 rule_holder_.domain_attrs.is_rtps_protected = true; 00208 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_RTPS_ORIGIN_AUTHENTICATED; 00209 } else if (ACE_OS::strcasecmp(attr_rpk, "ENCRYPT_WITH_ORIGIN_AUTHENTICATION") == 0) { 00210 rule_holder_.domain_attrs.is_rtps_protected = true; 00211 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_RTPS_ENCRYPTED; 00212 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_RTPS_ORIGIN_AUTHENTICATED; 00213 } 00214 xercesc::XMLString::release(&attr_rpk); 00215 00216 rule_holder_.domain_attrs.plugin_participant_attributes |= ::DDS::Security::PLUGIN_PARTICIPANT_SECURITY_ATTRIBUTES_FLAG_IS_VALID; 00217 00218 // Process topic rules 00219 00220 xercesc::DOMNodeList * topic_rules = xmlDoc->getElementsByTagName(XStr("topic_rule")); 00221 00222 for (XMLSize_t tr = 0; tr < topic_rules->getLength(); tr++) { 00223 xercesc::DOMNodeList * topic_rule_nodes = topic_rules->item(tr)->getChildNodes(); 00224 Governance::TopicAccessRule t_rules; 00225 00226 for (XMLSize_t trn = 0; trn < topic_rule_nodes->getLength(); trn++) { 00227 XStr tr_tag = topic_rule_nodes->item(trn)->getNodeName(); 00228 char * tr_val = xercesc::XMLString::transcode(topic_rule_nodes->item(trn)->getTextContent()); 00229 00230 if (tr_tag == "topic_expression") { 00231 t_rules.topic_expression = tr_val; 00232 } 00233 else if (tr_tag == "enable_discovery_protection") { 00234 t_rules.topic_attrs.is_discovery_protected = ACE_OS::strcasecmp(tr_val, "false") == 0 ? false : true; 00235 } 00236 else if (tr_tag == "enable_liveliness_protection") { 00237 t_rules.topic_attrs.is_liveliness_protected = ACE_OS::strcasecmp(tr_val, "false") == 0 ? false : true; 00238 } 00239 else if (tr_tag == "enable_read_access_control") { 00240 t_rules.topic_attrs.is_read_protected = ACE_OS::strcasecmp(tr_val, "false") == 0 ? false : true; 00241 } 00242 else if (tr_tag == "enable_write_access_control") { 00243 t_rules.topic_attrs.is_write_protected = ACE_OS::strcasecmp(tr_val, "false") == 0 ? false : true; 00244 } 00245 else if (tr_tag == "metadata_protection_kind") { 00246 t_rules.metadata_protection_kind.assign(tr_val); 00247 } 00248 else if (tr_tag == "data_protection_kind") { 00249 t_rules.data_protection_kind.assign(tr_val); 00250 } 00251 xercesc::XMLString::release(&tr_val); 00252 } 00253 rule_holder_.topic_rules.push_back(t_rules); 00254 } 00255 00256 access_rules_.push_back(rule_holder_); 00257 } // domain_rule 00258 00259 return 0; 00260 }
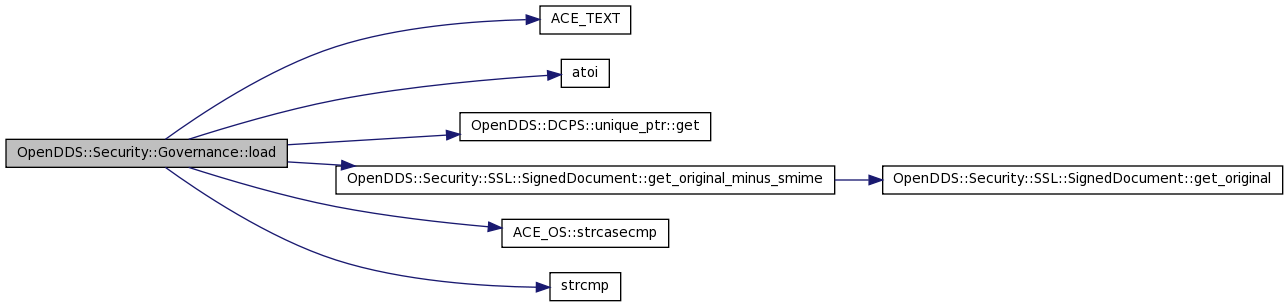
Definition at line 52 of file Governance.h.
Referenced by access_rules(), and load().
 1.6.1
1.6.1