Implements the DDS built-in version of the Authentication plugin for the DDS Security Specification. More...
#include <AuthenticationBuiltInImpl.h>
Implements the DDS built-in version of the Authentication plugin for the DDS Security Specification.
See the DDS security specification, OMG formal/17-09-20, for a description of the interface this class is implementing.
Definition at line 48 of file AuthenticationBuiltInImpl.h.
typedef std::map<DDS::Security::HandshakeHandle, HandshakeDataPair> OpenDDS::Security::AuthenticationBuiltInImpl::HandshakeDataMap [private] |
Definition at line 205 of file AuthenticationBuiltInImpl.h.
typedef std::pair<LocalParticipantData::shared_ptr, RemoteParticipantData::shared_ptr> OpenDDS::Security::AuthenticationBuiltInImpl::HandshakeDataPair [private] |
Definition at line 204 of file AuthenticationBuiltInImpl.h.
typedef std::map<DDS::Security::IdentityHandle, LocalParticipantData::shared_ptr> OpenDDS::Security::AuthenticationBuiltInImpl::LocalParticipantMap [private] |
Definition at line 199 of file AuthenticationBuiltInImpl.h.
typedef std::map<DDS::Security::IdentityHandle, RemoteParticipantData::shared_ptr> OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantMap [private] |
Definition at line 182 of file AuthenticationBuiltInImpl.h.
| OpenDDS::Security::AuthenticationBuiltInImpl::AuthenticationBuiltInImpl | ( | ) |
Definition at line 73 of file AuthenticationBuiltInImpl.cpp.
00074 : listener_ptr_() 00075 , identity_mutex_() 00076 , handshake_mutex_() 00077 , handle_mutex_() 00078 , next_handle_(1) 00079 { 00080 }
| OpenDDS::Security::AuthenticationBuiltInImpl::~AuthenticationBuiltInImpl | ( | ) | [virtual] |
Definition at line 82 of file AuthenticationBuiltInImpl.cpp.
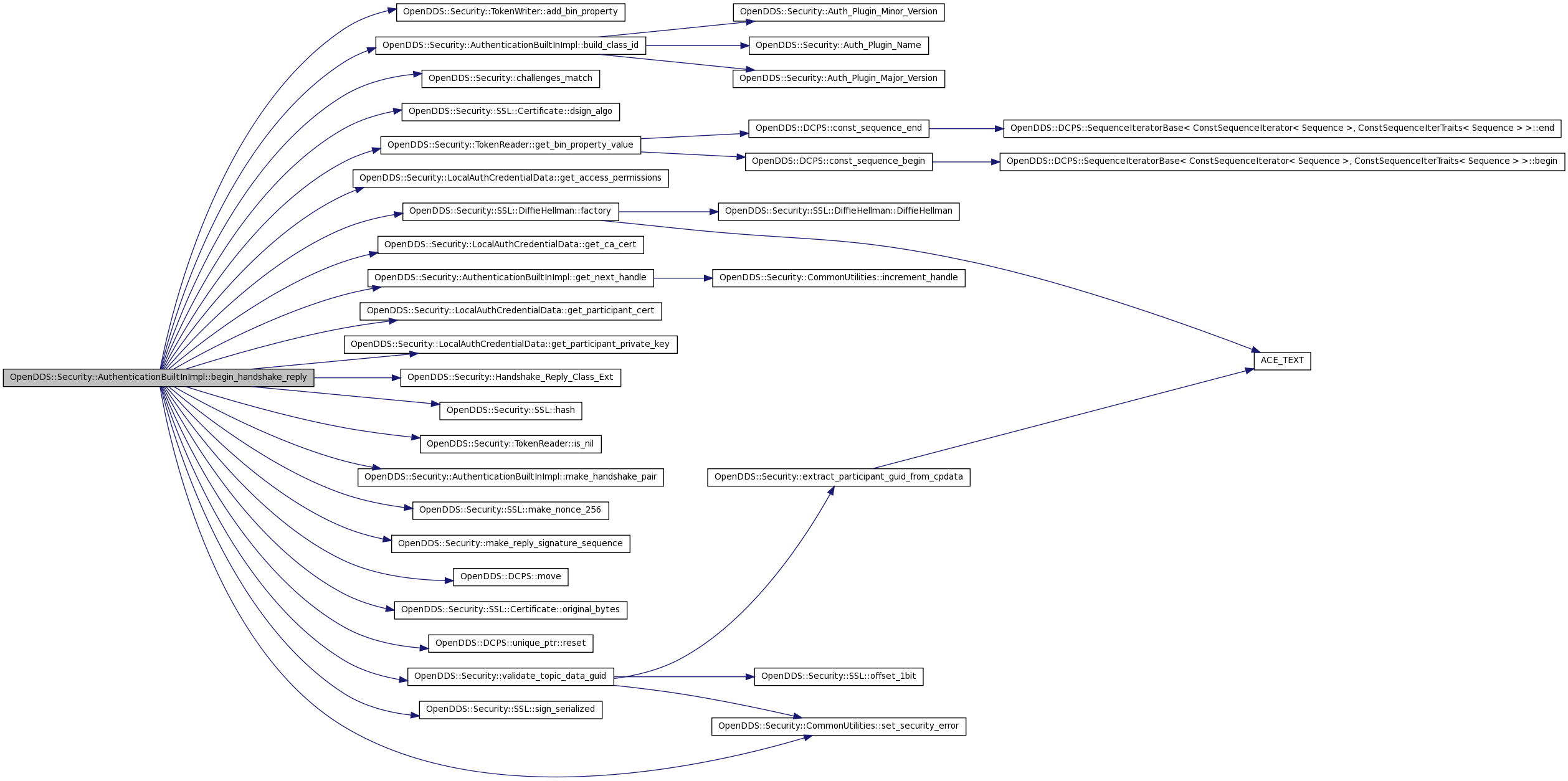
| DDS::Security::ValidationResult_t OpenDDS::Security::AuthenticationBuiltInImpl::begin_handshake_reply | ( | ::DDS::Security::HandshakeHandle & | handshake_handle, | |
| ::DDS::Security::HandshakeMessageToken & | handshake_message_out, | |||
| ::DDS::Security::IdentityHandle | initiator_identity_handle, | |||
| ::DDS::Security::IdentityHandle | replier_identity_handle, | |||
| const ::DDS::OctetSeq & | serialized_local_participant_data, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 592 of file AuthenticationBuiltInImpl.cpp.
References OpenDDS::Security::TokenWriter::add_bin_property(), build_class_id(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::c_perm, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::certificate, OpenDDS::Security::challenges_match(), OpenDDS::Security::AuthenticationBuiltInImpl::LocalParticipantData::credentials, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::diffie_hellman, OpenDDS::Security::SSL::Certificate::dsign_algo(), OpenDDS::Security::SSL::DiffieHellman::factory(), OpenDDS::Security::LocalAuthCredentialData::get_access_permissions(), OpenDDS::Security::TokenReader::get_bin_property_value(), OpenDDS::Security::LocalAuthCredentialData::get_ca_cert(), get_next_handle(), OpenDDS::Security::LocalAuthCredentialData::get_participant_cert(), OpenDDS::Security::LocalAuthCredentialData::get_participant_private_key(), handshake_data_, handshake_mutex_, OpenDDS::Security::Handshake_Reply_Class_Ext(), OpenDDS::Security::SSL::hash(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::hash_c1, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::hash_c2, identity_mutex_, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::initiator_identity, OpenDDS::Security::TokenReader::is_nil(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::local_auth_request, make_handshake_pair(), OpenDDS::Security::SSL::make_nonce_256(), OpenDDS::Security::make_reply_signature_sequence(), OpenDDS::DCPS::move(), OpenDDS::Security::SSL::Certificate::original_bytes(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::remote_auth_request, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::replier_identity, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::reply, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::request, OpenDDS::DCPS::unique_ptr< T, Deleter >::reset(), OpenDDS::Security::CommonUtilities::set_security_error(), OpenDDS::Security::SSL::sign_serialized(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::state, OpenDDS::Security::validate_topic_data_guid(), DDS::Security::VALIDATION_FAILED, and DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE.
00599 { 00600 using OpenDDS::Security::TokenWriter; 00601 using OpenDDS::Security::TokenReader; 00602 00603 ACE_Guard<ACE_Thread_Mutex> identity_data_guard(identity_mutex_); 00604 00605 // Copy the "in" part of the inout param 00606 const DDS::Security::HandshakeMessageToken request_token = handshake_message_out; 00607 handshake_message_out = DDS::Security::HandshakeMessageToken(); 00608 00609 DDS::OctetSeq challenge1, challenge2, dh2, cperm, hash_c1, hash_c2; 00610 00611 SSL::Certificate::unique_ptr remote_cert(new SSL::Certificate); 00612 SSL::DiffieHellman::unique_ptr diffie_hellman; 00613 00614 const DDS::Security::ValidationResult_t Failure = DDS::Security::VALIDATION_FAILED, 00615 Pending = DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE; 00616 00617 if (serialized_local_participant_data.length() == 0) { 00618 set_security_error(ex, -1, 0, "No participant data provided"); 00619 return Failure; 00620 } 00621 00622 HandshakeDataPair handshake_data = make_handshake_pair(initiator_identity_handle, replier_identity_handle); 00623 00624 if (! handshake_data.first) { 00625 set_security_error(ex, -1, 0, "Unknown local participant"); 00626 return DDS::Security::VALIDATION_FAILED; 00627 } 00628 00629 if (! handshake_data.second) { 00630 set_security_error(ex, -1, 0, "Unknown remote participant"); 00631 return DDS::Security::VALIDATION_FAILED; 00632 } 00633 00634 LocalParticipantData& local_data = *(handshake_data.first); 00635 RemoteParticipantData& remote_data = *(handshake_data.second); 00636 00637 DDS::Security::HandshakeMessageToken message_data_in(request_token); 00638 TokenReader message_in(message_data_in); 00639 if (message_in.is_nil()) { 00640 set_security_error(ex, -1, 0, "Handshake_message_out is an inout param and must not be nil"); 00641 return Failure; 00642 00643 } 00644 challenge1 = message_in.get_bin_property_value("challenge1"); 00645 00646 TokenReader initiator_remote_auth_request(remote_data.remote_auth_request); 00647 if (! initiator_remote_auth_request.is_nil()) { 00648 const DDS::OctetSeq& future_challenge = initiator_remote_auth_request.get_bin_property_value("future_challenge"); 00649 00650 if (! challenges_match(challenge1, future_challenge)) { 00651 return Failure; 00652 } 00653 } 00654 00655 const LocalAuthCredentialData& local_credential_data = *(local_data.credentials); 00656 00657 const DDS::OctetSeq& cid = message_in.get_bin_property_value("c.id"); 00658 if (cid.length() > 0) { 00659 00660 remote_cert->deserialize(cid); 00661 if (X509_V_OK != remote_cert->validate(local_credential_data.get_ca_cert())) 00662 { 00663 set_security_error(ex, -1, 0, "Certificate validation failed"); 00664 return Failure; 00665 } 00666 00667 } else { 00668 set_security_error(ex, -1, 0, "Certificate validation failed due to empty 'c.id' property supplied"); 00669 return Failure; 00670 } 00671 00672 /* Validate participant_guid in c.pdata */ 00673 00674 const DDS::OctetSeq& cpdata = message_in.get_bin_property_value("c.pdata"); 00675 00676 std::vector<unsigned char> hash; 00677 if (0 != remote_cert->subject_name_digest(hash)) { 00678 set_security_error(ex, -1, 0, "Failed to generate subject-name digest from remote certificate."); 00679 return Failure; 00680 } 00681 00682 if (! validate_topic_data_guid(cpdata, hash, ex)) { 00683 return Failure; 00684 } 00685 00686 cperm = message_in.get_bin_property_value("c.perm"); 00687 00688 const DDS::OctetSeq& dh_algo = message_in.get_bin_property_value("c.kagree_algo"); 00689 diffie_hellman.reset(SSL::DiffieHellman::factory(dh_algo)); 00690 00691 /* Compute hash_c1 and store for later */ 00692 00693 { 00694 CredentialHash hash(*remote_cert, 00695 *diffie_hellman, 00696 cpdata, 00697 cperm); 00698 int err = hash(hash_c1); 00699 if (err) { 00700 set_security_error(ex, -1, 0, "Failed to compute hash_c1."); 00701 return Failure; 00702 } 00703 } 00704 00705 /* Compute hash_c2 and store for later */ 00706 00707 { 00708 CredentialHash hash(local_credential_data.get_participant_cert(), 00709 *diffie_hellman, 00710 serialized_local_participant_data, 00711 local_credential_data.get_access_permissions()); 00712 int err = hash(hash_c2); 00713 if (err) { 00714 set_security_error(ex, -1, 0, "Failed to compute hash_c2."); 00715 return Failure; 00716 } 00717 } 00718 00719 // TODO: Currently support for OCSP is optional in the security spec and 00720 // so it has been deferred to a post-beta release. 00721 // Add OCSP checks when "ocsp_status" property is given in message_in. 00722 // Most of this logic would probably be placed in the Certificate directly 00723 // or an OCSP abstraction that the Certificate uses. 00724 00725 const DDS::OctetSeq& dh1 = message_in.get_bin_property_value("dh1"); 00726 00727 TokenWriter message_out(handshake_message_out, build_class_id(Handshake_Reply_Class_Ext)); 00728 00729 message_out.add_bin_property("c.id", local_credential_data.get_participant_cert().original_bytes()); 00730 message_out.add_bin_property("c.perm", local_credential_data.get_access_permissions()); 00731 message_out.add_bin_property("c.pdata", serialized_local_participant_data); 00732 message_out.add_bin_property("c.dsign_algo", local_credential_data.get_participant_cert().dsign_algo()); 00733 message_out.add_bin_property("c.kagree_algo", diffie_hellman->kagree_algo()); 00734 message_out.add_bin_property("hash_c2", hash_c2); 00735 00736 diffie_hellman->pub_key(dh2); 00737 message_out.add_bin_property("dh2", dh2); 00738 message_out.add_bin_property("hash_c1", hash_c1); 00739 message_out.add_bin_property("dh1", dh1); 00740 message_out.add_bin_property("challenge1", challenge1); 00741 00742 TokenReader initiator_local_auth_request(remote_data.local_auth_request); 00743 if (! initiator_local_auth_request.is_nil()) { 00744 const DDS::OctetSeq& future_challenge = initiator_local_auth_request.get_bin_property_value("future_challenge"); 00745 message_out.add_bin_property("challenge2", future_challenge); 00746 challenge2 = future_challenge; 00747 00748 } else { 00749 int err = SSL::make_nonce_256(challenge2); 00750 if (! err) { 00751 message_out.add_bin_property("challenge2", challenge2); 00752 00753 } else { 00754 set_security_error(ex, -1, 0, "SSL::make_nonce_256 failed."); 00755 return Failure; 00756 } 00757 } 00758 00759 DDS::BinaryPropertySeq sign_these; 00760 make_reply_signature_sequence(hash_c2, 00761 challenge2, 00762 dh2, 00763 challenge1, 00764 dh1, 00765 hash_c1, 00766 sign_these); 00767 00768 DDS::OctetSeq signature; 00769 SSL::sign_serialized(sign_these, local_credential_data.get_participant_private_key(), signature); 00770 message_out.add_bin_property("signature", signature); 00771 00772 remote_data.replier_identity = replier_identity_handle; 00773 remote_data.initiator_identity = initiator_identity_handle; 00774 remote_data.state = DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE; 00775 remote_data.diffie_hellman = DCPS::move(diffie_hellman); 00776 remote_data.certificate = DCPS::move(remote_cert); 00777 remote_data.c_perm = cperm; 00778 remote_data.reply = handshake_message_out; 00779 remote_data.request = request_token; 00780 remote_data.hash_c1 = hash_c1; 00781 remote_data.hash_c2 = hash_c2; 00782 00783 handshake_handle = get_next_handle(); 00784 { 00785 ACE_Guard<ACE_Thread_Mutex> guard(handshake_mutex_); 00786 handshake_data_[handshake_handle] = handshake_data; 00787 } 00788 00789 return Pending; 00790 }
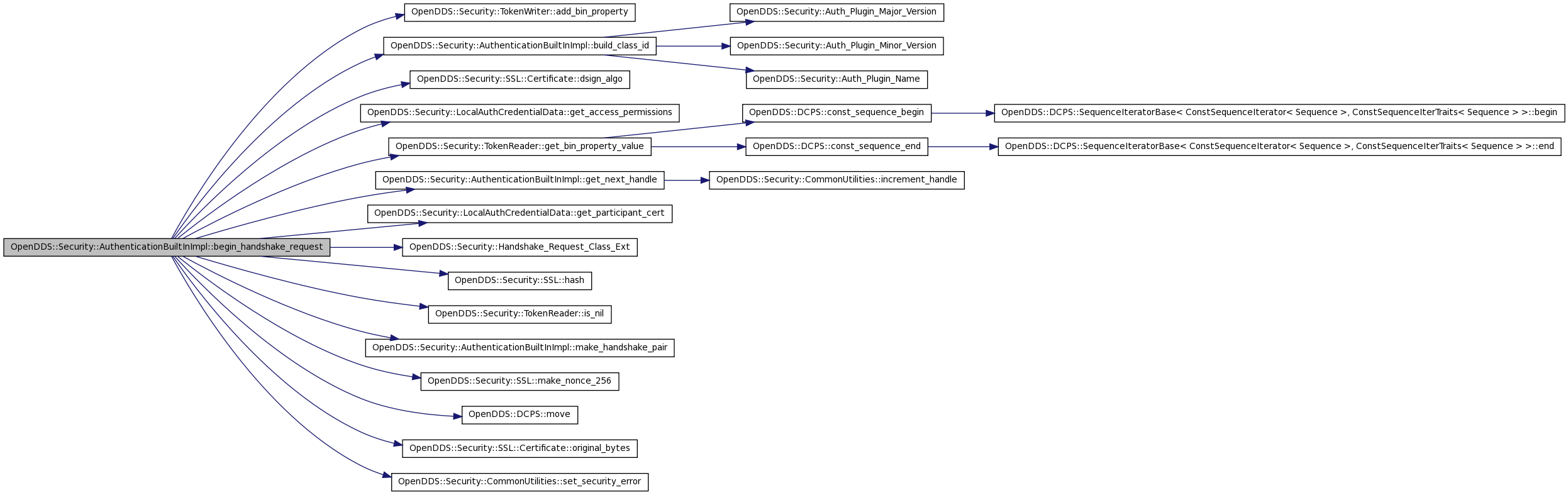
| DDS::Security::ValidationResult_t OpenDDS::Security::AuthenticationBuiltInImpl::begin_handshake_request | ( | ::DDS::Security::HandshakeHandle & | handshake_handle, | |
| ::DDS::Security::HandshakeMessageToken & | handshake_message, | |||
| ::DDS::Security::IdentityHandle | initiator_identity_handle, | |||
| ::DDS::Security::IdentityHandle | replier_identity_handle, | |||
| const ::DDS::OctetSeq & | serialized_local_participant_data, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 308 of file AuthenticationBuiltInImpl.cpp.
References OpenDDS::Security::TokenWriter::add_bin_property(), build_class_id(), OpenDDS::Security::AuthenticationBuiltInImpl::LocalParticipantData::credentials, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::diffie_hellman, OpenDDS::Security::SSL::Certificate::dsign_algo(), OpenDDS::Security::LocalAuthCredentialData::get_access_permissions(), OpenDDS::Security::TokenReader::get_bin_property_value(), get_next_handle(), OpenDDS::Security::LocalAuthCredentialData::get_participant_cert(), handshake_data_, handshake_mutex_, OpenDDS::Security::Handshake_Request_Class_Ext(), OpenDDS::Security::SSL::hash(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::hash_c1, identity_mutex_, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::initiator_identity, OpenDDS::Security::TokenReader::is_nil(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::local_auth_request, make_handshake_pair(), OpenDDS::Security::SSL::make_nonce_256(), OpenDDS::DCPS::move(), OpenDDS::Security::SSL::Certificate::original_bytes(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::replier_identity, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::reply, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::request, OpenDDS::Security::CommonUtilities::set_security_error(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::state, DDS::Security::VALIDATION_FAILED, and DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE.
00315 { 00316 if (serialized_local_participant_data.length() == 0) { 00317 set_security_error(ex, -1, 0, "No participant data provided"); 00318 return DDS::Security::VALIDATION_FAILED; 00319 } 00320 00321 ACE_Guard<ACE_Thread_Mutex> identity_data_guard(identity_mutex_); 00322 00323 HandshakeDataPair handshake_data = make_handshake_pair(initiator_identity_handle, replier_identity_handle); 00324 00325 if (! handshake_data.first) { 00326 set_security_error(ex, -1, 0, "Unknown local participant"); 00327 return DDS::Security::VALIDATION_FAILED; 00328 } 00329 00330 if (! handshake_data.second) { 00331 set_security_error(ex, -1, 0, "Unknown remote participant"); 00332 return DDS::Security::VALIDATION_FAILED; 00333 } 00334 00335 LocalParticipantData& local_data = *(handshake_data.first); 00336 RemoteParticipantData& remote_data = *(handshake_data.second); 00337 00338 const LocalAuthCredentialData& local_credential_data = *(local_data.credentials); 00339 00340 SSL::DiffieHellman::unique_ptr diffie_hellman(new SSL::DiffieHellman(new SSL::ECDH_PRIME_256_V1_CEUM)); 00341 00342 OpenDDS::Security::TokenWriter message_out(handshake_message, build_class_id(Handshake_Request_Class_Ext)); 00343 00344 // Compute hash_c1 and store for later 00345 00346 DDS::OctetSeq hash_c1; 00347 00348 { 00349 CredentialHash hash(local_credential_data.get_participant_cert(), 00350 *diffie_hellman, 00351 serialized_local_participant_data, 00352 local_credential_data.get_access_permissions()); 00353 00354 int err = hash(hash_c1); 00355 if (err) { 00356 set_security_error(ex, -1, 0, "Failed to generate credential-hash 'hash_c1'"); 00357 return DDS::Security::VALIDATION_FAILED; 00358 } 00359 } 00360 00361 message_out.add_bin_property("c.id", local_credential_data.get_participant_cert().original_bytes()); 00362 message_out.add_bin_property("c.perm", local_credential_data.get_access_permissions()); 00363 message_out.add_bin_property("c.pdata", serialized_local_participant_data); 00364 message_out.add_bin_property("c.dsign_algo", local_credential_data.get_participant_cert().dsign_algo()); 00365 message_out.add_bin_property("c.kagree_algo", diffie_hellman->kagree_algo()); 00366 message_out.add_bin_property("hash_c1", hash_c1); 00367 00368 DDS::OctetSeq dhpub; 00369 diffie_hellman->pub_key(dhpub); 00370 message_out.add_bin_property("dh1", dhpub); 00371 00372 OpenDDS::Security::TokenReader auth_wrapper(remote_data.local_auth_request); 00373 if (auth_wrapper.is_nil()) { 00374 DDS::OctetSeq nonce; 00375 int err = SSL::make_nonce_256(nonce); 00376 if (! err) { 00377 message_out.add_bin_property("challenge1", nonce); 00378 00379 } else { 00380 set_security_error(ex, -1, 0, "Failed to generate 256-bit nonce value for challenge1 property"); 00381 return DDS::Security::VALIDATION_FAILED; 00382 } 00383 00384 } else { 00385 const DDS::OctetSeq& challenge_data = auth_wrapper.get_bin_property_value("future_challenge"); 00386 message_out.add_bin_property("challenge1", challenge_data); 00387 00388 } 00389 00390 remote_data.initiator_identity = initiator_identity_handle; 00391 remote_data.replier_identity = replier_identity_handle; 00392 remote_data.state = DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE; 00393 remote_data.request = handshake_message; 00394 remote_data.reply = DDS::Security::Token(); 00395 remote_data.diffie_hellman = DCPS::move(diffie_hellman); 00396 remote_data.hash_c1 = hash_c1; 00397 00398 handshake_handle = get_next_handle(); 00399 { 00400 ACE_Guard<ACE_Thread_Mutex> identity_data_guard(handshake_mutex_); 00401 handshake_data_[handshake_handle] = handshake_data; 00402 } 00403 00404 return DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE; 00405 }
| std::string OpenDDS::Security::AuthenticationBuiltInImpl::build_class_id | ( | const std::string & | message_ext | ) | [private] |
Definition at line 1363 of file AuthenticationBuiltInImpl.cpp.
References OpenDDS::Security::Auth_Plugin_Major_Version(), OpenDDS::Security::Auth_Plugin_Minor_Version(), and OpenDDS::Security::Auth_Plugin_Name().
Referenced by begin_handshake_reply(), begin_handshake_request(), and process_handshake_reply().
01364 { 01365 std::stringstream class_id_stream; 01366 class_id_stream << Auth_Plugin_Name 01367 << ":" << Auth_Plugin_Major_Version 01368 << "." << Auth_Plugin_Minor_Version 01369 << "+" << message_ext; 01370 01371 return class_id_stream.str(); 01372 }

| bool OpenDDS::Security::AuthenticationBuiltInImpl::check_class_versions | ( | const char * | remote_class_id | ) | [private] |
Definition at line 1332 of file AuthenticationBuiltInImpl.cpp.
References OpenDDS::Security::Auth_Plugin_Major_Version(), OpenDDS::Security::Auth_Plugin_Name(), and major_version().
01333 { 01334 if (NULL == remote_class_id) { 01335 return false; 01336 } 01337 bool class_matches = false; 01338 01339 // Slow, but this is just for the stub 01340 std::string class_id_str(remote_class_id); 01341 01342 // Class name is the text prior to the final ':' 01343 size_t colon_pos = class_id_str.find_last_of(':'); 01344 if (std::string::npos != colon_pos && colon_pos > 0) { 01345 // Compare the class name vs the expected class name 01346 std::string remote_class_name = class_id_str.substr(0, colon_pos); 01347 if (0 == Auth_Plugin_Name.compare(remote_class_name)) { 01348 // Major version is the text between the final : and a . 01349 size_t major_start = colon_pos + 1; 01350 size_t period_pos = class_id_str.find_first_of('.', major_start); 01351 if (std::string::npos != period_pos && period_pos > major_start) { 01352 std::string major_version = class_id_str.substr(major_start, period_pos - major_start); 01353 if (0 == Auth_Plugin_Major_Version.compare(major_version)) { 01354 class_matches = true; 01355 } 01356 } 01357 } 01358 } 01359 01360 return class_matches; 01361 }
| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::get_authenticated_peer_credential_token | ( | ::DDS::Security::AuthenticatedPeerCredentialToken & | peer_credential_token, | |
| ::DDS::Security::HandshakeHandle | handshake_handle, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 845 of file AuthenticationBuiltInImpl.cpp.
References OpenDDS::Security::Auth_Peer_Cred_Token_Class_Id(), DDS::Security::DataHolder::binary_properties, get_handshake_data(), handshake_mutex_, DDS::BinaryProperty_t::name, DDS::BinaryProperty_t::propagate, OpenDDS::Security::CommonUtilities::set_security_error(), state, DDS::Security::VALIDATION_OK, DDS::Security::VALIDATION_OK_FINAL_MESSAGE, and DDS::BinaryProperty_t::value.
00849 { 00850 using namespace DDS::Security; 00851 ::CORBA::Boolean result = false; 00852 00853 ACE_Guard<ACE_Thread_Mutex> handshake_data_guard(handshake_mutex_); 00854 00855 HandshakeDataPair handshake_data = get_handshake_data(handshake_handle); 00856 if (handshake_data.first && handshake_data.second) { 00857 ValidationResult_t state = handshake_data.second->state; 00858 if (state == VALIDATION_OK || state == VALIDATION_OK_FINAL_MESSAGE) { 00859 OpenDDS::Security::TokenWriter peer_token(peer_credential_token, Auth_Peer_Cred_Token_Class_Id); 00860 00861 DDS::BinaryPropertySeq& props = peer_credential_token.binary_properties; 00862 props.length(2); 00863 00864 DDS::BinaryProperty_t p1; 00865 p1.name = "c.id"; 00866 p1.value = handshake_data.second->certificate->original_bytes(); 00867 p1.propagate = true; 00868 00869 DDS::BinaryProperty_t p2; 00870 p2.name = "c.perm"; 00871 p2.value = handshake_data.second->c_perm; 00872 p2.propagate = true; 00873 00874 props[0] = p1; 00875 props[1] = p2; 00876 00877 result = true; 00878 00879 } else { 00880 set_security_error(ex, -1, 0, "Validation state must be either VALIDATION_OK or VALIDATION_OK_FINAL_MESSAGE"); 00881 } 00882 00883 } else { 00884 set_security_error(ex, -1, 0, "Unknown handshake handle"); 00885 } 00886 00887 return result; 00888 }
| std::string OpenDDS::Security::AuthenticationBuiltInImpl::get_extension | ( | const char * | class_id | ) | [private] |
Definition at line 1374 of file AuthenticationBuiltInImpl.cpp.
Referenced by process_handshake().
01375 { 01376 std::string ext_string(""); 01377 01378 std::string class_id_str(class_id); 01379 size_t extension_delim_pos = class_id_str.find_last_of('+'); 01380 if (extension_delim_pos != std::string::npos) { 01381 size_t start_ext_pos = extension_delim_pos + 1; 01382 if (start_ext_pos < class_id_str.length()) { 01383 ext_string = class_id_str.substr(start_ext_pos); 01384 } 01385 } 01386 01387 return ext_string; 01388 }

| AuthenticationBuiltInImpl::HandshakeDataPair OpenDDS::Security::AuthenticationBuiltInImpl::get_handshake_data | ( | DDS::Security::HandshakeHandle | handle | ) | [private] |
Definition at line 1283 of file AuthenticationBuiltInImpl.cpp.
References handshake_data_.
Referenced by get_authenticated_peer_credential_token(), get_shared_secret(), process_final_handshake(), and process_handshake_reply().
01284 { 01285 HandshakeDataMap::iterator found = handshake_data_.find(handle); 01286 if (found != handshake_data_.end()) { 01287 return found->second; 01288 } 01289 01290 return HandshakeDataPair(); 01291 }
| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::get_identity_status_token | ( | ::DDS::Security::IdentityStatusToken & | identity_status_token, | |
| ::DDS::Security::IdentityHandle | handle, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 173 of file AuthenticationBuiltInImpl.cpp.
References get_local_participant(), identity_mutex_, OpenDDS::Security::CommonUtilities::set_security_error(), and status.
00177 { 00178 ::CORBA::Boolean status = false; 00179 00180 ACE_Guard<ACE_Thread_Mutex> identity_data_guard(identity_mutex_); 00181 00182 // Populate a simple version of an IdentityStatusToken as long as the handle is known 00183 LocalParticipantData::shared_ptr local_data = get_local_participant(handle); 00184 if (local_data) { 00185 00186 // TODO: Pending AuthenticationListener support (see security spec. 8.3.2.2). 00187 // This routine will most likely populate the IdentityStatusToken with 00188 // useful data once this has been completed. For now it's a glorified no-op! 00189 00190 status = true; 00191 } else { 00192 set_security_error(ex, -1, 0, "Unknown Identity handle"); 00193 } 00194 00195 return status; 00196 }

| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::get_identity_token | ( | ::DDS::Security::IdentityToken & | identity_token, | |
| ::DDS::Security::IdentityHandle | handle, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 137 of file AuthenticationBuiltInImpl.cpp.
References OpenDDS::Security::TokenWriter::add_property(), OpenDDS::Security::LocalAuthCredentialData::get_ca_cert(), get_local_participant(), OpenDDS::Security::LocalAuthCredentialData::get_participant_cert(), identity_mutex_, OpenDDS::Security::SSL::Certificate::keypair_algo(), OpenDDS::Security::CommonUtilities::set_security_error(), status, and OpenDDS::Security::SSL::Certificate::subject_name_to_str().
00141 { 00142 ::CORBA::Boolean status = false; 00143 00144 ACE_Guard<ACE_Thread_Mutex> identity_data_guard(identity_mutex_); 00145 00146 LocalParticipantData::shared_ptr local_data = get_local_participant(handle); 00147 if (local_data) { 00148 const LocalAuthCredentialData& local_credential_data = *(local_data->credentials); 00149 00150 const SSL::Certificate& pcert = local_credential_data.get_participant_cert(); 00151 const SSL::Certificate& cacert = local_credential_data.get_ca_cert(); 00152 00153 std::string tmp; 00154 00155 OpenDDS::Security::TokenWriter identity_wrapper(identity_token, "DDS:Auth:PKI-DH:1.0"); 00156 00157 pcert.subject_name_to_str(tmp); 00158 identity_wrapper.add_property("dds.cert.sn", tmp.c_str()); 00159 identity_wrapper.add_property("dds.cert.algo", pcert.keypair_algo()); 00160 00161 cacert.subject_name_to_str(tmp); 00162 identity_wrapper.add_property("dds.ca.sn", tmp.c_str()); 00163 identity_wrapper.add_property("dds.ca.algo", cacert.keypair_algo()); 00164 00165 status = true; 00166 00167 } else { 00168 set_security_error(ex, -1, 0, "Unknown Identity handle"); 00169 } 00170 return status; 00171 }
| AuthenticationBuiltInImpl::LocalParticipantData::shared_ptr OpenDDS::Security::AuthenticationBuiltInImpl::get_local_participant | ( | DDS::Security::IdentityHandle | handle | ) | [private] |
Definition at line 1272 of file AuthenticationBuiltInImpl.cpp.
References local_participants_.
Referenced by get_identity_status_token(), get_identity_token(), and set_permissions_credential_and_token().
01273 { 01274 LocalParticipantMap::iterator found = local_participants_.find(handle); 01275 if (found != local_participants_.end()) { 01276 return found->second; 01277 } 01278 01279 return LocalParticipantData::shared_ptr(); 01280 }
| CORBA::Long OpenDDS::Security::AuthenticationBuiltInImpl::get_next_handle | ( | ) | [private] |
Definition at line 1390 of file AuthenticationBuiltInImpl.cpp.
References handle_mutex_, OpenDDS::Security::CommonUtilities::increment_handle(), and next_handle_.
Referenced by begin_handshake_reply(), and begin_handshake_request().
01391 { 01392 ACE_Guard<ACE_Thread_Mutex> guard(handle_mutex_); 01393 return CommonUtilities::increment_handle(next_handle_); 01394 }


| DDS::Security::SharedSecretHandle * OpenDDS::Security::AuthenticationBuiltInImpl::get_shared_secret | ( | ::DDS::Security::HandshakeHandle | handshake_handle, | |
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 816 of file AuthenticationBuiltInImpl.cpp.
References get_handshake_data(), handshake_mutex_, OpenDDS::Security::CommonUtilities::set_security_error(), state, DDS::Security::VALIDATION_OK, and DDS::Security::VALIDATION_OK_FINAL_MESSAGE.
00819 { 00820 using namespace DDS::Security; 00821 00822 SharedSecretHandle* result = 0; 00823 00824 ACE_Guard<ACE_Thread_Mutex> handshake_data_guard(handshake_mutex_); 00825 00826 HandshakeDataPair handshake_data = get_handshake_data(handshake_handle); 00827 if (handshake_data.first && handshake_data.second) { 00828 00829 ValidationResult_t state = handshake_data.second->state; 00830 if (state == VALIDATION_OK || state == VALIDATION_OK_FINAL_MESSAGE) { 00831 SharedSecretHandle_var handle = handshake_data.second->shared_secret; 00832 result = handle._retn(); 00833 00834 } else { 00835 set_security_error(ex, -1, 0, "Validation state must be either VALIDATION_OK or VALIDATION_OK_FINAL_MESSAGE"); 00836 } 00837 00838 } else { 00839 set_security_error(ex, -1, 0, "Unknown handshake handle"); 00840 } 00841 00842 return result; 00843 }

| bool OpenDDS::Security::AuthenticationBuiltInImpl::is_handshake_initiator | ( | const DCPS::GUID_t & | local, | |
| const DCPS::GUID_t & | remote | |||
| ) | [private] |
Definition at line 1321 of file AuthenticationBuiltInImpl.cpp.
01322 { 01323 const unsigned char* local_ = reinterpret_cast<const unsigned char*>(&local); 01324 const unsigned char* remote_ = reinterpret_cast<const unsigned char*>(&remote); 01325 01326 /* if remote > local, pending request; else pending handshake message */ 01327 return std::lexicographical_compare(local_, local_ + sizeof(local), 01328 remote_, remote_ + sizeof(remote)); 01329 01330 }
| AuthenticationBuiltInImpl::HandshakeDataPair OpenDDS::Security::AuthenticationBuiltInImpl::make_handshake_pair | ( | DDS::Security::IdentityHandle | h1, | |
| DDS::Security::IdentityHandle | h2 | |||
| ) | [private] |
Finds the local and remote data objects associated with h1 and h2 and creates a new handshake pair with them. It does not matter which handle is local and which is remote.
| h1 | Either a local or remote handle. | |
| h2 | Either a local or remote handle. |
Definition at line 1294 of file AuthenticationBuiltInImpl.cpp.
References DDS::HANDLE_NIL, and local_participants_.
Referenced by begin_handshake_reply(), and begin_handshake_request().
01296 { 01297 DDS::Security::IdentityHandle other = DDS::HANDLE_NIL; 01298 01299 LocalParticipantMap::iterator found_local = local_participants_.find(h1); 01300 if (found_local != local_participants_.end()) { 01301 other = h2; 01302 01303 } else { 01304 found_local = local_participants_.find(h2); 01305 if (found_local != local_participants_.end()) { 01306 other = h1; 01307 01308 } else { 01309 return HandshakeDataPair(); 01310 } 01311 } 01312 01313 RemoteParticipantMap::iterator found_remote = found_local->second->validated_remotes.find(other); 01314 if (found_remote != found_local->second->validated_remotes.end()) { 01315 return std::make_pair(found_local->second, found_remote->second); 01316 } 01317 01318 return HandshakeDataPair(); 01319 }

| DDS::Security::ValidationResult_t OpenDDS::Security::AuthenticationBuiltInImpl::process_final_handshake | ( | const DDS::Security::HandshakeMessageToken & | handshake_message_in, | |
| DDS::Security::HandshakeHandle | handshake_handle, | |||
| DDS::Security::SecurityException & | ex | |||
| ) | [private] |
Definition at line 1177 of file AuthenticationBuiltInImpl.cpp.
References OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::certificate, OpenDDS::Security::challenges_match(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::diffie_hellman, OpenDDS::Security::TokenReader::get_bin_property_value(), get_handshake_data(), handshake_mutex_, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::hash_c1, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::hash_c2, identity_mutex_, OpenDDS::Security::TokenReader::is_nil(), OpenDDS::Security::make_final_signature_sequence(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::reply, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::request, OpenDDS::Security::CommonUtilities::set_security_error(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::shared_secret, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::state, DDS::Security::VALIDATION_FAILED, DDS::Security::VALIDATION_OK, DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE, and OpenDDS::Security::SSL::verify_serialized().
Referenced by process_handshake().
01181 { 01182 const DDS::Security::ValidationResult_t Failure = DDS::Security::VALIDATION_FAILED; 01183 const DDS::Security::ValidationResult_t ValidationOkay = DDS::Security::VALIDATION_OK; 01184 01185 ACE_Guard<ACE_Thread_Mutex> handshake_data_guard(handshake_mutex_); 01186 ACE_Guard<ACE_Thread_Mutex> identity_data_guard(identity_mutex_); 01187 01188 HandshakeDataPair handshake_data = get_handshake_data(handshake_handle); 01189 if (!handshake_data.first || !handshake_data.second) { 01190 set_security_error(ex, -1, 0, "Unknown handshake handle"); 01191 return Failure; 01192 } 01193 01194 RemoteParticipantData& remote_data = *(handshake_data.second); 01195 01196 if (remote_data.state != DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE) { 01197 set_security_error(ex, -1, 0, "Handshake state is not valid"); 01198 return Failure; 01199 } 01200 01201 /* Check challenge1 and challenge2 match what was sent with the reply-message-token */ 01202 01203 TokenReader handshake_final_token(handshake_message_in); 01204 if (handshake_final_token.is_nil()) { 01205 set_security_error(ex, -1, 0, "Handshake-final-token is nil"); 01206 return Failure; 01207 } 01208 01209 TokenReader handshake_reply_token(remote_data.reply); 01210 if (handshake_reply_token.is_nil()) { 01211 set_security_error(ex, -1, 0, "Handshake-reply-token is nil"); 01212 return Failure; 01213 } 01214 01215 /* Per the spec, dh1 is optional in all _but_ the request token so it's grabbed from the request */ 01216 TokenReader handshake_request_token(remote_data.request); 01217 if (handshake_reply_token.is_nil()) { 01218 set_security_error(ex, -1, 0, "Handshake-reply-token is nil"); 01219 return Failure; 01220 } 01221 01222 const DDS::OctetSeq& dh1 = handshake_request_token.get_bin_property_value("dh1"); 01223 const DDS::OctetSeq& dh2 = handshake_reply_token.get_bin_property_value("dh2"); 01224 01225 const DDS::OctetSeq& challenge1_reply = handshake_reply_token.get_bin_property_value("challenge1"); 01226 const DDS::OctetSeq& challenge2_reply = handshake_reply_token.get_bin_property_value("challenge2"); 01227 01228 const DDS::OctetSeq& challenge1_final = handshake_final_token.get_bin_property_value("challenge1"); 01229 const DDS::OctetSeq& challenge2_final = handshake_final_token.get_bin_property_value("challenge2"); 01230 01231 if (! challenges_match(challenge1_reply, challenge1_final) || ! challenges_match(challenge2_reply, challenge2_final)) { 01232 return Failure; 01233 } 01234 01235 /* Validate Signature field */ 01236 01237 const SSL::Certificate::unique_ptr& remote_cert = remote_data.certificate; 01238 01239 DDS::BinaryPropertySeq verify_these; 01240 make_final_signature_sequence(remote_data.hash_c1, 01241 challenge1_reply, 01242 dh1, 01243 challenge2_reply, 01244 dh2, 01245 remote_data.hash_c2, 01246 verify_these); 01247 01248 const DDS::OctetSeq& remote_signature = handshake_final_token.get_bin_property_value("signature"); 01249 01250 int err = SSL::verify_serialized(verify_these, *remote_cert, remote_signature); 01251 if (err) { 01252 set_security_error(ex, -1, 0, "Remote 'signature' field failed signature verification"); 01253 return Failure; 01254 } 01255 01256 /* Compute/Store the Diffie-Hellman shared-secret */ 01257 01258 if (0 != remote_data.diffie_hellman->gen_shared_secret(dh1)) { 01259 set_security_error(ex, -1, 0, "Failed to generate shared secret from dh2 and dh1"); 01260 return Failure; 01261 } 01262 01263 remote_data.state = DDS::Security::VALIDATION_OK; 01264 remote_data.shared_secret = new SharedSecret(challenge1_reply, 01265 challenge2_reply, 01266 remote_data.diffie_hellman->get_shared_secret()); 01267 01268 return ValidationOkay; 01269 }

| DDS::Security::ValidationResult_t OpenDDS::Security::AuthenticationBuiltInImpl::process_handshake | ( | ::DDS::Security::HandshakeMessageToken & | handshake_message_out, | |
| const ::DDS::Security::HandshakeMessageToken & | handshake_message_in, | |||
| ::DDS::Security::HandshakeHandle | handshake_handle, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 792 of file AuthenticationBuiltInImpl.cpp.
References get_extension(), OpenDDS::Security::Handshake_Final_Class_Ext(), OpenDDS::Security::Handshake_Reply_Class_Ext(), process_final_handshake(), process_handshake_reply(), and DDS::Security::VALIDATION_OK.
00797 { 00798 // - SecurityException is populated if VALIDATION_FAILED 00799 DDS::Security::ValidationResult_t result = DDS::Security::VALIDATION_OK; 00800 00801 // Handle differently based on which direction this handshake is going 00802 std::string incoming_class_ext = get_extension(handshake_message_in.class_id); 00803 00804 if (0 == Handshake_Reply_Class_Ext.compare(incoming_class_ext)) 00805 { 00806 result = process_handshake_reply(handshake_message_out, handshake_message_in, handshake_handle, ex); 00807 } 00808 else if (0 == Handshake_Final_Class_Ext.compare(incoming_class_ext)) 00809 { 00810 result = process_final_handshake(handshake_message_in, handshake_handle, ex); 00811 } 00812 00813 return result; 00814 }
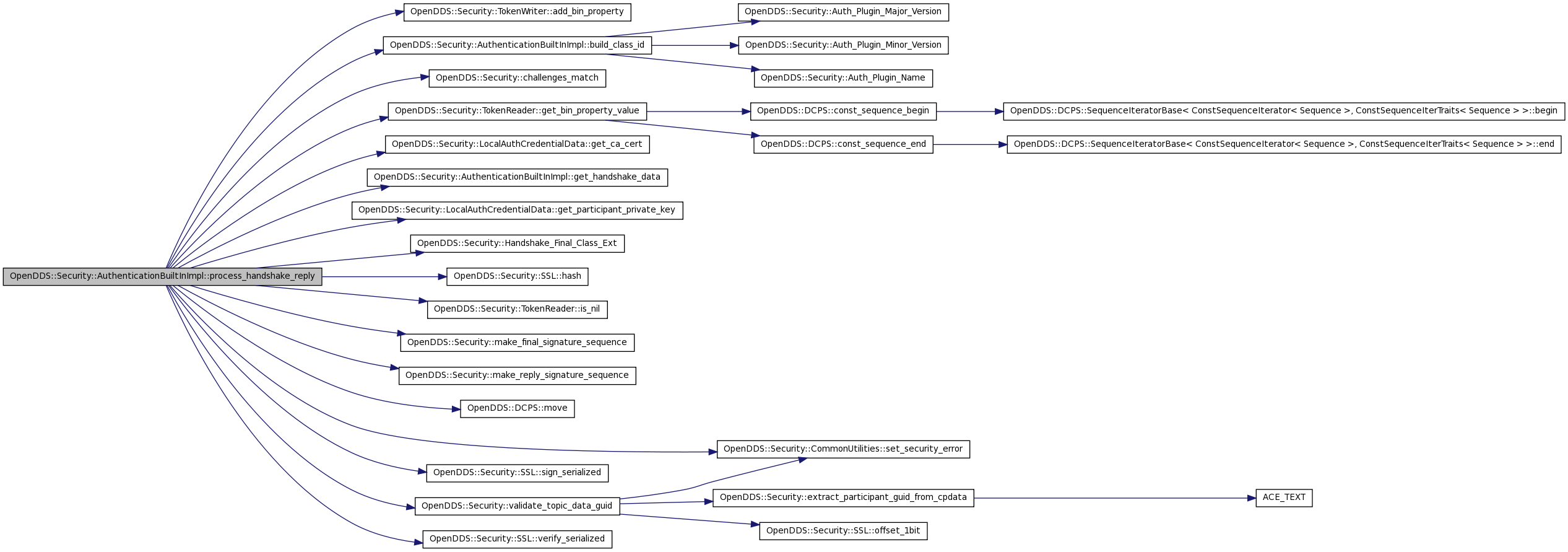
| DDS::Security::ValidationResult_t OpenDDS::Security::AuthenticationBuiltInImpl::process_handshake_reply | ( | DDS::Security::HandshakeMessageToken & | handshake_message_out, | |
| const DDS::Security::HandshakeMessageToken & | handshake_message_in, | |||
| DDS::Security::HandshakeHandle | handshake_handle, | |||
| DDS::Security::SecurityException & | ex | |||
| ) | [private] |
Definition at line 988 of file AuthenticationBuiltInImpl.cpp.
References OpenDDS::Security::TokenWriter::add_bin_property(), build_class_id(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::c_perm, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::certificate, OpenDDS::Security::challenges_match(), OpenDDS::Security::AuthenticationBuiltInImpl::LocalParticipantData::credentials, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::diffie_hellman, OpenDDS::Security::TokenReader::get_bin_property_value(), OpenDDS::Security::LocalAuthCredentialData::get_ca_cert(), get_handshake_data(), OpenDDS::Security::LocalAuthCredentialData::get_participant_private_key(), OpenDDS::Security::Handshake_Final_Class_Ext(), handshake_mutex_, OpenDDS::Security::SSL::hash(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::hash_c1, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::hash_c2, identity_mutex_, OpenDDS::Security::TokenReader::is_nil(), OpenDDS::Security::make_final_signature_sequence(), OpenDDS::Security::make_reply_signature_sequence(), OpenDDS::DCPS::move(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::remote_auth_request, OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::request, OpenDDS::Security::CommonUtilities::set_security_error(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::shared_secret, OpenDDS::Security::SSL::sign_serialized(), OpenDDS::Security::AuthenticationBuiltInImpl::RemoteParticipantData::state, OpenDDS::Security::validate_topic_data_guid(), DDS::Security::VALIDATION_FAILED, DDS::Security::VALIDATION_OK_FINAL_MESSAGE, DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE, and OpenDDS::Security::SSL::verify_serialized().
Referenced by process_handshake().
00993 { 00994 00995 ACE_Guard<ACE_Thread_Mutex> handshake_data_guard(handshake_mutex_); 00996 ACE_Guard<ACE_Thread_Mutex> identity_data_guard(identity_mutex_); 00997 00998 DDS::OctetSeq challenge1, hash_c2; 00999 SSL::Certificate::unique_ptr remote_cert(new SSL::Certificate); 01000 01001 const DDS::Security::ValidationResult_t Failure = DDS::Security::VALIDATION_FAILED; 01002 const DDS::Security::ValidationResult_t FinalMessage = DDS::Security::VALIDATION_OK_FINAL_MESSAGE; 01003 01004 HandshakeDataPair handshake_data = get_handshake_data(handshake_handle); 01005 if (!handshake_data.first || !handshake_data.second) { 01006 set_security_error(ex, -1, 0, "Unknown handshake handle"); 01007 return Failure; 01008 } 01009 01010 LocalParticipantData& local_data = *(handshake_data.first); 01011 RemoteParticipantData& remote_data = *(handshake_data.second); 01012 01013 if (remote_data.state != DDS::Security::VALIDATION_PENDING_HANDSHAKE_MESSAGE) { 01014 set_security_error(ex, -1, 0, "Handshake state is not valid"); 01015 return Failure; 01016 } 01017 01018 TokenReader message_in(handshake_message_in); 01019 if (message_in.is_nil()) { 01020 set_security_error(ex, -1, 0, "Handshake_message_in must not be nil"); 01021 return Failure; 01022 } 01023 01024 const DDS::OctetSeq& challenge2 = message_in.get_bin_property_value("challenge2"); 01025 01026 TokenReader auth_wrapper(remote_data.remote_auth_request); 01027 if (! auth_wrapper.is_nil()) { 01028 const DDS::OctetSeq& future_challenge = auth_wrapper.get_bin_property_value("future_challenge"); 01029 01030 if (! challenges_match(challenge2, future_challenge)) { 01031 set_security_error(ex, -1, 0, "challenge2 does not match future_challenge"); 01032 return Failure; 01033 } 01034 } 01035 01036 const LocalAuthCredentialData& local_credential_data = *(local_data.credentials); 01037 01038 const DDS::OctetSeq& cid = message_in.get_bin_property_value("c.id"); 01039 if (cid.length() > 0) { 01040 01041 remote_cert->deserialize(cid); 01042 01043 if (X509_V_OK != remote_cert->validate(local_credential_data.get_ca_cert())) 01044 { 01045 set_security_error(ex, -1, 0, "Certificate validation failed"); 01046 return Failure; 01047 } 01048 01049 } else { 01050 set_security_error(ex, -1, 0, "Certificate validation failed due to empty 'c.id' property supplied"); 01051 return Failure; 01052 } 01053 01054 /* Check that challenge1 on message_in matches the one sent in HandshakeRequestMessageToken */ 01055 01056 TokenReader handshake_request_token(remote_data.request); 01057 if (handshake_request_token.is_nil()) { 01058 set_security_error(ex, -1, 0, "Handshake-request-token is nil"); 01059 return Failure; 01060 01061 } else { 01062 challenge1 = handshake_request_token.get_bin_property_value("challenge1"); 01063 const DDS::OctetSeq& challenge1_reply = message_in.get_bin_property_value("challenge1"); 01064 01065 if (! challenges_match(challenge1, challenge1_reply)) { 01066 set_security_error(ex, -1, 0, "handshake-request challenge1 value does not match local challenge1"); 01067 return Failure; 01068 } 01069 } 01070 01071 /* Validate participant_guid in c.pdata */ 01072 01073 const DDS::OctetSeq& cpdata = message_in.get_bin_property_value("c.pdata"); 01074 01075 std::vector<unsigned char> hash; 01076 if (0 != remote_cert->subject_name_digest(hash)) { 01077 set_security_error(ex, -1, 0, "Failed to generate subject-name digest from remote certificate."); 01078 return Failure; 01079 } 01080 01081 if (! validate_topic_data_guid(cpdata, hash, ex)) { 01082 return Failure; 01083 } 01084 01085 /* Compute/Store the Diffie-Hellman shared-secret */ 01086 01087 const DDS::OctetSeq& dh2 = message_in.get_bin_property_value("dh2"); 01088 if (0 != remote_data.diffie_hellman->gen_shared_secret(dh2)) { 01089 set_security_error(ex, -1, 0, "Failed to generate shared secret from dh1 and dh2"); 01090 return Failure; 01091 } 01092 01093 const DDS::OctetSeq& cperm = message_in.get_bin_property_value("c.perm"); 01094 01095 /* Compute hash_c2 and store for later (hash_c1 was already computed in request) */ 01096 01097 { 01098 CredentialHash hash(*remote_cert, 01099 *remote_data.diffie_hellman, 01100 cpdata, 01101 cperm); 01102 int err = hash(hash_c2); 01103 if (err) { 01104 set_security_error(ex, -1, 0, "Computing hash_c2 failed"); 01105 return Failure; 01106 } 01107 } 01108 01109 /* Validate Signature field */ 01110 const DDS::OctetSeq& dh1 = handshake_request_token.get_bin_property_value("dh1"); 01111 01112 DDS::BinaryPropertySeq verify_these; 01113 make_reply_signature_sequence(hash_c2, 01114 challenge2, 01115 dh2, 01116 challenge1, 01117 dh1, 01118 remote_data.hash_c1, 01119 verify_these); 01120 01121 const DDS::OctetSeq& remote_signature = message_in.get_bin_property_value("signature"); 01122 01123 int err = SSL::verify_serialized(verify_these, *remote_cert, remote_signature); 01124 if (err) { 01125 set_security_error(ex, -1, 0, "Remote 'signature' field failed signature verification"); 01126 return Failure; 01127 } 01128 01129 OpenDDS::Security::TokenWriter final_msg(handshake_message_out, build_class_id(Handshake_Final_Class_Ext)); 01130 01131 final_msg.add_bin_property("hash_c1", remote_data.hash_c1); 01132 final_msg.add_bin_property("hash_c2", hash_c2); 01133 final_msg.add_bin_property("dh1", dh1); 01134 final_msg.add_bin_property("dh2", dh2); 01135 final_msg.add_bin_property("challenge1", challenge1); 01136 final_msg.add_bin_property("challenge2", challenge2); 01137 01138 DDS::BinaryPropertySeq sign_these; 01139 make_final_signature_sequence(remote_data.hash_c1, 01140 challenge1, 01141 dh1, 01142 challenge2, 01143 dh2, 01144 hash_c2, 01145 sign_these); 01146 01147 DDS::OctetSeq tmp; 01148 SSL::sign_serialized(sign_these, local_credential_data.get_participant_private_key(), tmp); 01149 final_msg.add_bin_property("signature", tmp); 01150 01151 remote_data.certificate = DCPS::move(remote_cert); 01152 remote_data.state = FinalMessage; 01153 remote_data.c_perm = message_in.get_bin_property_value("c.perm"); 01154 remote_data.hash_c2 = hash_c2; 01155 remote_data.shared_secret = new SharedSecret(challenge1, 01156 challenge2, 01157 remote_data.diffie_hellman->get_shared_secret()); 01158 return FinalMessage; 01159 }

| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::return_authenticated_peer_credential_token | ( | const ::DDS::Security::AuthenticatedPeerCredentialToken & | peer_credential_token, | |
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 927 of file AuthenticationBuiltInImpl.cpp.
| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::return_handshake_handle | ( | ::DDS::Security::HandshakeHandle | handshake_handle, | |
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 937 of file AuthenticationBuiltInImpl.cpp.
References handshake_data_, handshake_mutex_, and OpenDDS::Security::CommonUtilities::set_security_error().
00940 { 00941 ACE_Guard<ACE_Thread_Mutex> guard(handshake_mutex_); 00942 00943 HandshakeDataMap::iterator found = handshake_data_.find(handshake_handle); 00944 if (found != handshake_data_.end()) { 00945 handshake_data_.erase(found); 00946 return true; 00947 } 00948 00949 set_security_error(ex, -1, 0, "Handshake handle not recognized"); 00950 return false; 00951 }

| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::return_identity_handle | ( | ::DDS::Security::IdentityHandle | identity_handle, | |
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 953 of file AuthenticationBuiltInImpl.cpp.
References identity_mutex_, local_participants_, and OpenDDS::Security::CommonUtilities::set_security_error().
00956 { 00957 ACE_Guard<ACE_Thread_Mutex> guard(identity_mutex_); 00958 00959 LocalParticipantMap::iterator local = local_participants_.find(identity_handle); 00960 if (local != local_participants_.end()) { 00961 local_participants_.erase(local); 00962 return true; 00963 } 00964 00965 local = std::find_if(local_participants_.begin(), local_participants_.end(), 00966 local_has_remote_handle(identity_handle)); 00967 00968 if (local != local_participants_.end()) { 00969 local->second->validated_remotes.erase(identity_handle); 00970 return true; 00971 } 00972 00973 set_security_error(ex, -1, 0, "Identity handle not recognized"); 00974 return false; 00975 }

| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::return_identity_status_token | ( | const ::DDS::Security::IdentityStatusToken & | token, | |
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 916 of file AuthenticationBuiltInImpl.cpp.
| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::return_identity_token | ( | const ::DDS::Security::IdentityToken & | token, | |
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 905 of file AuthenticationBuiltInImpl.cpp.
| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::return_sharedsecret_handle | ( | ::DDS::Security::SharedSecretHandle * | sharedsecret_handle, | |
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 977 of file AuthenticationBuiltInImpl.cpp.
| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::set_listener | ( | ::DDS::Security::AuthenticationListener_ptr | listener, | |
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 890 of file AuthenticationBuiltInImpl.cpp.
References listener_ptr_, and OpenDDS::Security::CommonUtilities::set_security_error().
00893 { 00894 ::CORBA::Boolean results = false; 00895 00896 if (NULL == listener) { 00897 set_security_error(ex, -1, 0, "Null listener provided"); 00898 } else { 00899 results = true; 00900 listener_ptr_ = listener; 00901 } 00902 return results; 00903 }

| CORBA::Boolean OpenDDS::Security::AuthenticationBuiltInImpl::set_permissions_credential_and_token | ( | ::DDS::Security::IdentityHandle | handle, | |
| const ::DDS::Security::PermissionsCredentialToken & | permissions_credential, | |||
| const ::DDS::Security::PermissionsToken & | permissions_token, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 198 of file AuthenticationBuiltInImpl.cpp.
References get_local_participant(), identity_mutex_, and OpenDDS::Security::CommonUtilities::set_security_error().
00203 { 00204 ACE_UNUSED_ARG(permissions_token); 00205 00206 ACE_Guard<ACE_Thread_Mutex> identity_data_guard(identity_mutex_); 00207 00208 LocalParticipantData::shared_ptr local_data = get_local_participant(handle); 00209 if (! local_data) { 00210 set_security_error(ex, -1, 0, "Identity handle not recognized"); 00211 return false; 00212 } 00213 00214 return local_data->credentials->load_access_permissions(permissions_credential, ex); 00215 }

| virtual ::DDS::Security::ValidationResult_t OpenDDS::Security::AuthenticationBuiltInImpl::validate_local_identity | ( | ::DDS::Security::IdentityHandle & | local_identity_handle, | |
| DCPS::GUID_t & | adjusted_participant_guid, | |||
| ::DDS::Security::DomainId_t | domain_id, | |||
| const ::DDS::DomainParticipantQos & | participant_qos, | |||
| const DCPS::GUID_t & | candidate_participant_guid, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
| virtual ::DDS::Security::ValidationResult_t OpenDDS::Security::AuthenticationBuiltInImpl::validate_remote_identity | ( | ::DDS::Security::IdentityHandle & | remote_identity_handle, | |
| ::DDS::Security::AuthRequestMessageToken & | local_auth_request_token, | |||
| const ::DDS::Security::AuthRequestMessageToken & | remote_auth_request_token, | |||
| ::DDS::Security::IdentityHandle | local_identity_handle, | |||
| const ::DDS::Security::IdentityToken & | remote_identity_token, | |||
| const DCPS::GUID_t & | remote_participant_guid, | |||
| ::DDS::Security::SecurityException & | ex | |||
| ) |
Definition at line 268 of file AuthenticationBuiltInImpl.h.
Referenced by get_next_handle().
Definition at line 206 of file AuthenticationBuiltInImpl.h.
Referenced by begin_handshake_reply(), begin_handshake_request(), get_handshake_data(), and return_handshake_handle().
Definition at line 267 of file AuthenticationBuiltInImpl.h.
Referenced by begin_handshake_reply(), begin_handshake_request(), get_authenticated_peer_credential_token(), get_shared_secret(), process_final_handshake(), process_handshake_reply(), and return_handshake_handle().
Definition at line 266 of file AuthenticationBuiltInImpl.h.
Referenced by begin_handshake_reply(), begin_handshake_request(), get_identity_status_token(), get_identity_token(), process_final_handshake(), process_handshake_reply(), return_identity_handle(), and set_permissions_credential_and_token().
DDS::Security::AuthenticationListener_ptr OpenDDS::Security::AuthenticationBuiltInImpl::listener_ptr_ [private] |
Definition at line 264 of file AuthenticationBuiltInImpl.h.
Referenced by set_listener().
Definition at line 200 of file AuthenticationBuiltInImpl.h.
Referenced by get_local_participant(), make_handshake_pair(), and return_identity_handle().
Definition at line 270 of file AuthenticationBuiltInImpl.h.
Referenced by get_next_handle().
 1.6.1
1.6.1